Welcome to authentik
About authentik technical documentation
Our tech docs cover the typical topics, from installation to configuration, adding providers, defining policies and creating login flows, event monitoring, security, and attributes. Enterprise version documentation is included here, within our standard tech docs.
-
For information about integrating a specific application or software into authentik, refer to our Integrations section, accessible from the top menu-bar.
-
For developer-focused documentation, such as using our APIs and blueprints, setting up your development environment, translations, or how to contribute, refer to the Developer area, accessible from the top menu-bar.
What is authentik?
authentik is an open-source Identity Provider, focused on flexibility and versatility. With authentik, site administrators, application developers, and security engineers have a dependable and secure solution for authentication in almost any type of environment. There are robust recovery actions available for the users and applications, including user profile and password management. You can quickly edit, deactivate, or even impersonate a user profile, and set a new password for new users or reset an existing password.
You can use authentik in an existing environment to add support for new protocols, so introducing authentik to your current tech stack doesn't present re-architecting challenges. We already support all of the major providers, such as OAuth2, SAML, LDAP, and SCIM, so you can pick the protocol that you need for each application.
The authentik product provides the following consoles:
-
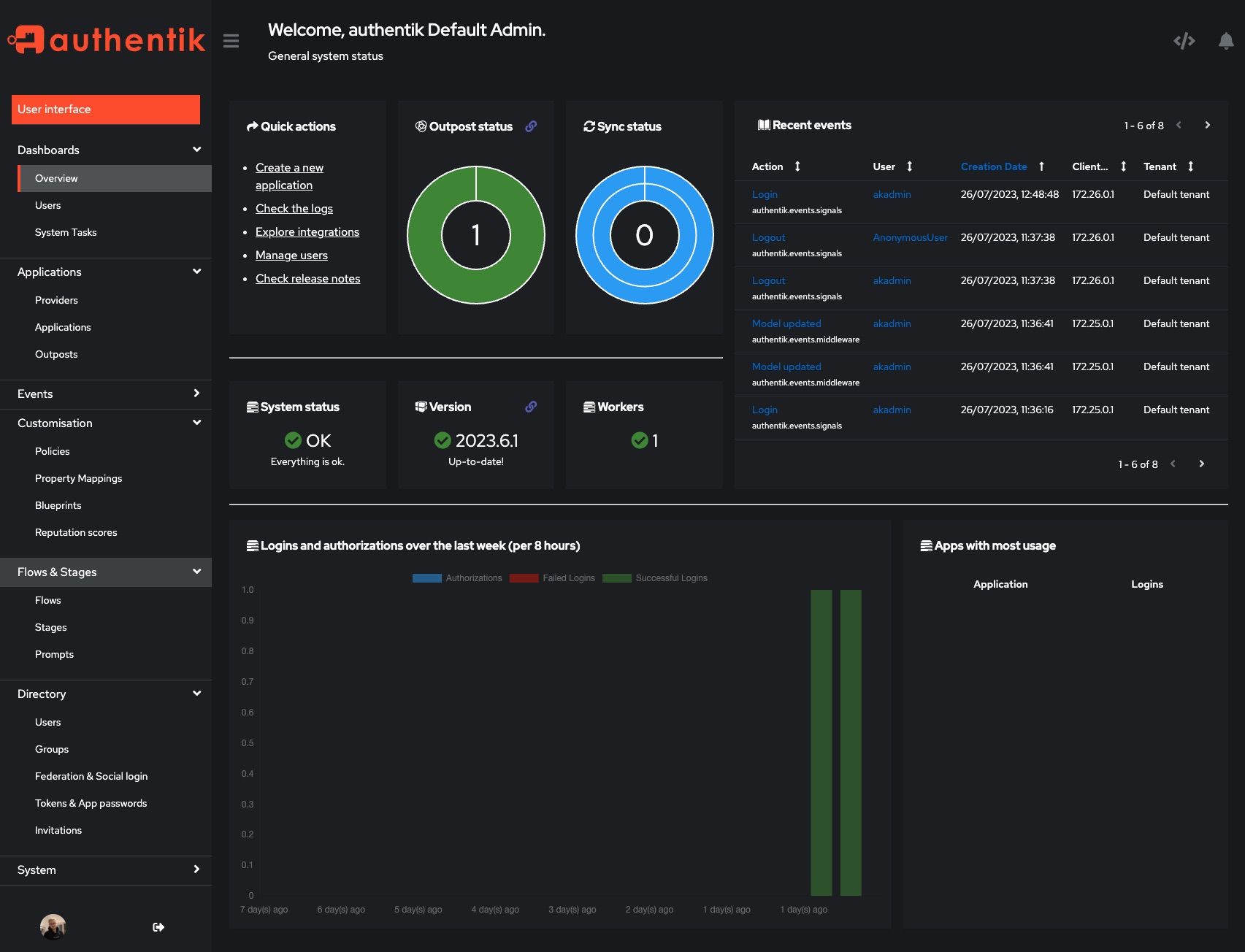
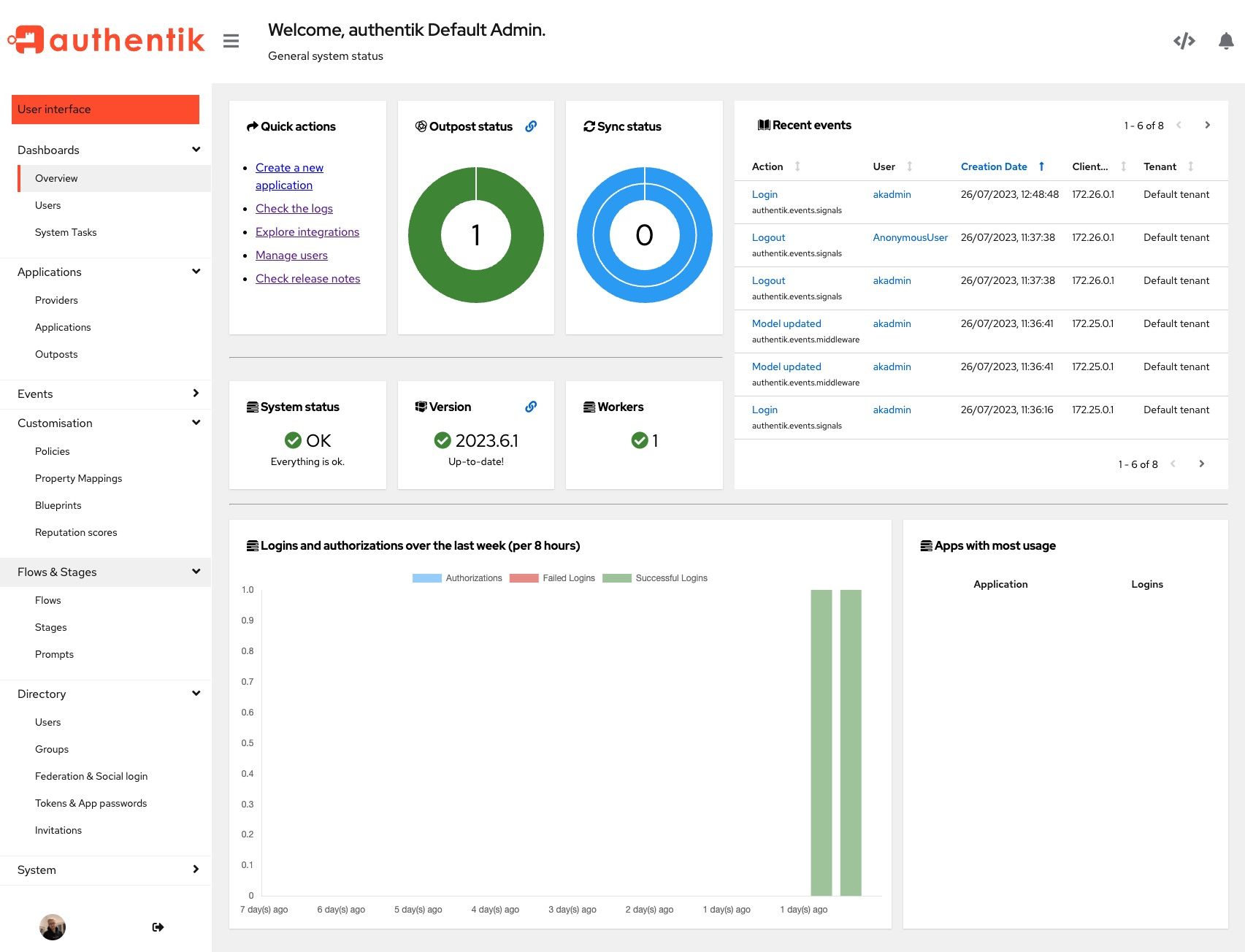
Admin interface: a visual tool for the creation and management of users and groups, tokens and credentials, application integrations, events, and the Flows that define standard and customizable login and authentication processes. Easy-to-read visual dashboards display system status, recent logins and authentication events, and application usage.
-
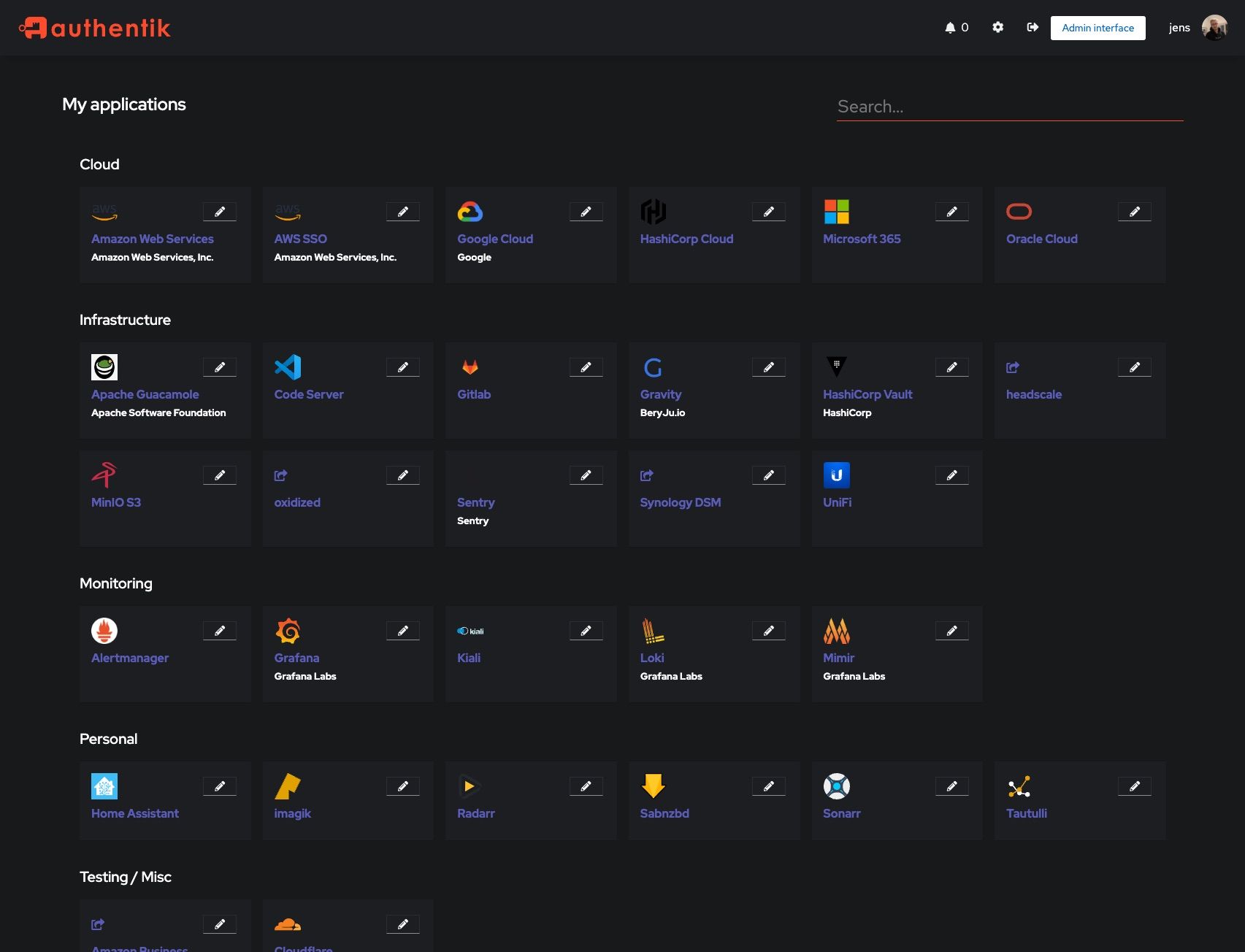
User interface: this console view in authentik displays all of the applications and integrations in which you have implemented authentik. Click on the app that you want to access to open it, or drill down to edit its configuration in the admin interface
-
Flows: Flows are the steps by which the various Stages of a login and authentication process occurs. A stage represents a single verification or logic step in the sign-on process. authentik allows for the customization and exact definition of these flows.
Installation
Refer to the installation steps in either Docker-compose or Kubernetes.
For more information about configuration, Beta versions, and additional installation options, see our main Installation section.
Screenshots
authentik can use Light or Dark mode for the Admin interface, User interface and the flow interface.